OSCP & CPTS in 1~ year from scratch
A retrospective on where I started and where I am now.
How it started
In late 2023 when my employer announced it would be closing sometime in 2025 I had a think about what I wanted to do with my future. At 32 so far I had a successful career mainly working as an electrical engineer and more recently working as an operations technician in oil and gas. I thought I would be quite happy going back to electrical engineering but I also felt like I had reached the limit of the career without going into management or getting a degree, the main issue was that it felt like there was no more to learn by going back into that industry. As a person that thrives on learning new things maybe I could look into an industry that is constantly evolving requiring you to keep learning.
By chance I came across an article written by a former colleague that had made the move into pentesting, the only reason this came up was due to use of the company name within the article. After reading my interest was instantly peaked, back in my teens I intended to either pursue a career in engineering or computing but I was offered an engineering apprenticeship so that was the route that I took. I had been interested in computers for a long time ever since getting my first hand me down system back when Windows 98 was the most modern operating system, I had mainly used computers for gaming but when I was interested in maybe looking into a career in game development I ended up learning some very basic C++ and playing around with software like Cheat Engine though even gaming back in the early days involved troubleshooting and messing with configuration files. I reached out to this former colleague to ask him more questions about it, in turn he provided me with a full roadmap of what I needed to learn and certifications to work towards. This information was invaluable and though I did tweak things it set the path that I would follow over the next year and a bit.
This colleague now runs the ESKILL8 discord community which is aimed at helping people get into cyber security check them out here : ESKILL8
Getting Started
January 24 : Firstly I started doing the CompTIA ITF+ which is a fundamental certification going over the basics of IT, I wanted to complete this certification to make sure this was a career switch I was going to be happy and willing to undertake. I figured that if I didn’t enjoy working on this then there was no point of carrying on. CompTIA are currently in the process of rebranding this to Tech+ so it might see some improvements.
Was it worth the money? Not really
Would I recommend it? Probably not unless you are curious about moving into IT
Did I learn something? Yes, Databases are confusing when you know nothing about them!
Around this time I also downloaded and set up my first Kali Linux VM. I have no Linux experience at all at this point so its going to be a rough journey!
With a kali VM up and running I also started working on the basics on TryHackme, I was already aware of Hack The Box at this point and had a quick look at it but the material covered at this point was just way over my head and far too difficult, though I was able to fire MS-017-010 off against a couple of boxes using Metasploit which was good fun.
The TryHackMe paths I did were : Pre Security, Cyber Security 101 and the Jr Penetration Tester (though I only did 40% of this one).
Summary : At this point I had some basics basics down and could tackle some of the easiest boxes on TryHackMe from my Kali VM. I passed the IFT+ exam and was looking into what was next as I was keen to progress further.
My recommendation : If you want to get started from scratch then do not bother looking at Hack The Box until you have covered most of the basics on TryHackMe as the HTB material expects you to have a baseline knowledge. I believe they are taking steps to try and reduce this gap though so things might change.
Progress
February 2024 : There is a saying that goes something like "You don't know what you don't know" and at this point I didn't know a lot, one of these things I didn’t know about was NETWORKING!. This was the next step on trying to improve my skills and knowledge to give myself a decent fundamental baseline to build off.
My intention was to study for and complete the CompTIA Network+ certification, So I grabbed the Total Seminars Net+ course off Udemy and some practice exams and got to work… Then I realised I was not a big fan of video courses and completing just the Udemy course took until June! During this time I tried to keep my skills up doing small bits and pieces on TryHackMe but I was slowly drifting away due to the grind of going through the Net+ material.
June 2024: Well eventually I made it through the Network+ material, though it was a grind I learned a lot and it turns out IT is a lot more complex than most people think, and this is coming from someone who has been using computers daily for 20~ years. The subject goes way deeper than most people expect. I had completed the practice exam and instead of sending the real exam I decided to start on something else… HackTheBox CPTS
Though I found networking interesting at this point I was glad to be back doing something that I enjoyed which kept me motivated to continue working on it every day and in all my spare time. This was a massive step up in difficulty but I pushed through and conducted additional research where I felt I needed it. The course is amazing for the price and the amount of knowledge packed into this certification is incredible but I will touch on that later.
October 2024 : Well what a journey, I finally completed the CPTS path after completing the final module Attacking Enterprise Networks blind. I was now eligible to sit the exam so what did I do? Nothing for 2 months. Around this time from October into December I had to get an operation to have my Gallbladder removed and the surgeon must have been having a bad day because he made me significantly worse requiring another operation in December. Thankfully this is all fixed now but this in combination with feeling like I wasn’t ready for the exam resulted in me not doing much for 2 months. I did work on some boxes here and there but not too much.
December 2024 : After my second operation I was “fixed” and ready to go for the exam, around this time I started working on every single easy and medium box on HTB and also did 80% of the Dante Prolab. This was me shaking off the rust after 2 months of not doing anything and I was surprised that I had somehow managed to retain most of the material covered in the CPTS path. I worked on improving my methodology and note taking while getting more and more exposure to different exploits, vulnerabilities and technologies. Though I dont feel like any of this extra work would have been required if I had just sat the exam after finishing the path, I think that it really helped as I discovered some new tools and techniques that were outside the scope of the CPTS course.
Achieving your goals
January 25 : On the 23rd of January I started the CPTS exam. In all honesty I decided just to go for it, there were still doubts in my mind that I was ready for it but sometimes you just need to take the leap. I can’t say much about the exam obviously but I can tell you that it is HARD, Many people including professional pentesters either require multiple attempts or scrape through with the bare minimum 12/14 flags. After taking 25 hours to get the first flag I thought there was no way that I was going to pass, I was doomed. But I kept trying and after 6.5 days I had acquired the full 14/14 set of flags and began working on the report, I could not bring myself just to leave it at the minimum 12/14 required to pass as it would feel like leaving the challenge half completed. I then spent the next 2 days working on writing up a professional grade pentest report which I submitted on the Friday evening with 1.5 days left on the clock. I was confident that I could not improve the report any more, it was just over 200 pages long with a clear executive summary and an extremely detailed technical walkthrough I had gave it my all. I came out of this exam feeling that I had significantly improved my skills during it and I felt like I almost knew what I was doing (at least a tiny bit).
February 2025 : Waiting for the CPTS results was hell. The service level agreement with HTB is up to 20 business days, for me it was just under this. During the wait time I had continued working on all the active easy and medium machines improving my skills but every day I was waiting for the email to come in to tell me if I had passed or failed.
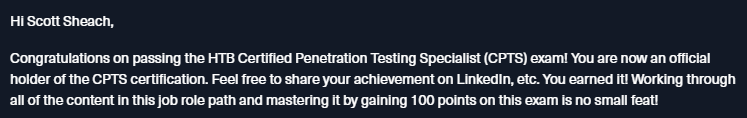
After submitting the report on the 31st January on the 21st February it finally arrived!
I was ecstatic and very proud that I had managed to achieve this, After the usual linkedin post and informing people in discord I was thinking, What's next? I knew I wanted to do the OSCP but did I have time to commit to doing it since its an extremely expensive course at just under £1500.
Well luckily I didn’t need to make that decision now as while I was waiting for the CPTS results I actually had booked and been studying for the CompTIA Security+ exam for 2 weeks and the exam was only a few days away on Feb 26th. I was back to video courses on Udemy as I had picked up the Jason Dion Sec+ course at the same time I had purchased the Network+ course almost a year ago! This time things went a bit smoother, I found the content more engaging since it seemed more relevant (and I didn't need to calculate subnets anymore). I passed this with no issue though during the exam I was almost certain that I was about to recieve a failure after finishing but you just need to keep your cool and do your best.
Two days later on Feb 28th I purchased the OSCP 90 days package, Rip bank balance.
March 2025 : At this point I was solely focused on working towards improving my skills and ensuring that I was going to pass the OSCP on the first attempt. During this time I ended up joining a team on Hack The Box so that I could could start collaborating on more difficult boxes and learn from others who are more experienced than myself.
In the mean time I was blasting through the OSCP content as much of it was just the same stuff covered in CPTS with less detail. I did stop and take detailed notes at some sections which were not covered in CPTS but more on that later.
Towards the end of March Hack The Box were hosting the Cyber Apocalypse CTF challenge which I took part in with my team. I contributed to the team by completing all the AI prompt injection tasks and helped out with some OSINT challenge, unfortunately due to being pretty fresh there wasn’t much that I could do to assist with some of the more crazy challenges like machine learning and reverse engineering. But it was great fun and we placed 115th out of over 8000 teams. Not bad for us having less than half the maximum team size!
After the CTF event I continued working on the OSCP challenge labs and picked up a one month subscription for Proving Grounds so I could work through some of the boxes on the LainKusanagi list of recommended machines, I had already done quite a lot of the machines in the HTB section so I focused on the Offsec boxes.
Much like with the CPTS I decided to book the exam for when I had some time off work on a whim, the 10th of April. Again sometimes you just need to take the leap otherwise you will find yourself in an endless loop of "I need to do X before I can do Y".
April 2025 : Well it was finally time. For such a big achievement like completing the OSCP here it feels like a footnote, Everything went fine. The exam was significantly easier than the CPTS exam though I would not call it “easy”. I had acquired 80/100 points required to pass within 6 hours which is more than the required pass mark of 70/100.
Obviously though I was going for the 100/100! I spent the next 4~ hours on the last machine which turned out to have a technical issue, Once I decided to ask support about it they investigated and resolved it within 15 minutes. 30 Minutes later I had completed the final flag scoring 100/100 points. I started at 1300 and finished at 0130, This included a few breaks and having a meal so not too bad when you consider how much time the technical issue ate up.
On reporting there isn’t too much to say, It was completed in around 4 hours and it was sent off for review. Big props to Offsec as I had my results back under 24 hours informing me that I had passed, Not quite the same nervous wait I had experienced with the CPTS! Since this is the new assumed breach format I guess I got two certs, OSCP and OSCP+.
After completing OSCP in a month all the goals I set just over a year earlier were complete, I still can’t believe it. But I found myself asking again… What now?
The Future
With what I feel is a good skill set under my belt I feel like I am now in a position to apply for a job in the industry, I finish with current employer at the end of June so I am now applying for positions looking to start after that time. I know the job market is competitive so I am not expecting much but in the mean while I will continue to work on rounding out my skill set. At the moment my plan is to start learning some python to aid in automation and this will also help with creating my own custom exploit scripts in the future. After that I would like to learn a bit more about cloud pentesting, It was covered in OSCP but I would like to go deeper into it and also improve my skills on web applications.
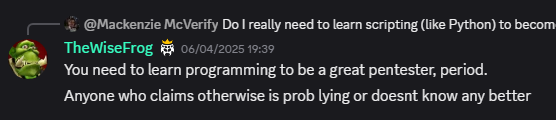
TheWiseFrog once said…
Closing Thoughts
If you want to replicate this your mileage may vary, I have a strong background in fault finding and problem solving from working as an electrical engineer for over a decade though I had no formal IT experience before I started. If you are interested in changing career paths you should consider the value of cross-skills that you have gained in your previous career and leverage them to make things as easy as possible. Also just put the time in even 1-2 hours every day will add up over time, its a marathon not a sprint.
In the grand scheme of things this is really only the start for me as I look to now make the switch into the industry, Though this whole blog post might sound like a success story I'm still just starting out.
If you are hiring in the UK and would like to chat or if you would like to connect feel free to get in touch on Linkedin.
But wait…
CPTS vs OSCP as a noob - The part you actually came here for!
Now that you’ve been forced to read all that you can read the part you actually care about.
Content
CPTS : The amount and depth of the content here is incredible. It really covers everything to take you from minimum knowledge to being a competent pentester. I don’t think you will find such a comprehensive selection of material anywhere else. It does have some bad points like Password attacks and there are some questions that feel a bit unfair but overall this is the gold standard. This course will teach you how to manually exploit vulnerabilities without relying on CVE’s and POC’s off github.
OSCP : The quality of the material just isn’t up to the same standard as CPTS. Though this is the case there are concepts covered in this course that are not covered in the CPTS such as phishing techniques and there is a full new AWS section that is actually incredibly good, Its not worth paying the price just for the AWS section but you can see that Offsec have put a lot of effort into it and it would be nice to see the rest of the course get the same treatment.
WINNER : CPTS , though I feel like the new Offsec modules (AWS) are on par with CPTS.
Labs
CPTS : Aside from some issues with some super slow labs during Pivoting? (I think), the labs are solid never had any issues. You can also boot these up at any time you like after completing the module including the ‘Attacking Enterprise Networks’ capstone labs. I feel like another capstone lab with slightly harder difficulty than AEN would help people prepare better as I felt that there was quite a jump.
OSCP : So I will only comment on the Challenge labs that come with the course since Proving grounds are a different thing and I skipped pretty much all of the module labs aside from the AWS/Phishing ones. The labs are really good, I really enjoyed them all especially Challenge labs 0-2. The course actually comes with many labs that are beyond the scope of the exam but I have still have 2 months access left so I might have a go at them.
WINNER : OSCP - I’m comparing the module labs to OSCP challenge labs so this might not be fair but CPTS doesn’t give you anything to work on after finishing AEN without purchasing prolabs or doing boxes on the main platform, with OSCP you are getting a ton and they also have advanced capstone labs in the modules too!
Exam
CPTS : This is a 10 day long exam in which you have to complete a full grey box pentest of a simulated enterprise network and complete the report, Prepare to feel like you have just wasted a year of your time when you come to sitting this exam as it will make you feel like you know nothing. But if you can make it through you will be a better pentester for it. There are no tool restrictions here, you can drop a C2 if you like (yes I’ve seen someone ask if this is allowed). Everything you need to know is covered within the course material, though I found getting some more AD experience with some of the more recent windows boxes helped to improve my skills beyond the course which helped. Waiting up-to 20 days for results sucks.
OSCP : For this exam you have 24 hours to compromise the machines and another 24 hours to write your report. As much as some people like to flame Offsec and the OSCP this exam is not a pushover and I can easily see how people get caught out. There are tool restrictions in place here so just stick to the basics. I also had a technical issue during the exam which cost me around 4~ hours but it was quickly fixed within 15 minutes after asking them to investigate. The agreement for results is 10 business days but they were provided in less than 24h and on a Saturday good job!
WINNER : Exam environment - CPTS , Results waiting time - OSCP
Reporting
It's not all about about hacking boxes, if you want to be a pentester reporting is a big part of the job and both these certifications come with reporting requirements.
CPTS : Requires a full professional grade report. This took me 2 days to complete, You still have access to the exam environment during this so you can go back to improve your notes and take better screenshots or get whatever information you feel like you might need.
OSCP : The reporting requirements are still quite strict for this and you no longer have access to the environment when you are writing it so make sure you have every single command and screenshot that you are going to need otherwise you are going to be in trouble!
WINNER : No winner here - If you want to learn how to write a proper report please check out this article from an00brektn - An Objectively Opinionated Look at Report Writing (for Penetration Testing) If you follow his advice you will not go wrong.
Price
Nothing to say here
WINNER : CPTS
TLDR / Conclusion
So at this point I’ve written a lot of words so you are probably wondering when I’m going to stop or maybe even which certification you should work towards…
What cert should I do? : Well I think you should do BOTH.
Start with CPTS and then do OSCP, CPTS is going to give you the knowledge but the certification isn’t widely recognised yet meanwhile OSCP is on every single job advert (in the UK at least). If you can only afford one and you wish to pursue a career then honestly going for OSCP might be the better option, but if you can afford OSCP then you can probably also afford CPTS too! As CPTS gains more recognition the OSCP might not be required anymore but until then you can choose to go with the system or go against it.
If you are starting from scratch then start with TryHackMe and follow a similar path that I have outlined in this post. Make sure you also cover some basic networking, you dont need to study for Net+ like I did but it will help you greatly as you progress into attacking Active Directory networks and you need to pivot and port forward.
And the most important thing is to keep going and not give up, a little bit every day adds up over time. Remember its a marathon, Not a sprint.
As mentioned previously if you are hiring in the UK and would like to chat about potential roles or if you would like to connect feel free to get in touch on Linkedin.
Thanks for reading!
PS. Imagine writing a blog post in 2025 with no AI, Crazy right?